
A prominent vehicle-for-hire and parcel delivery company based in Pakistan, Bykea, has suffered a significant data breach which affected its extensive user database.
The SafetyDetectives cybersecurity team, led by head researcher Anurag Sen, discovered the elastic server vulnerability during routine IP-address checks on specific ports.
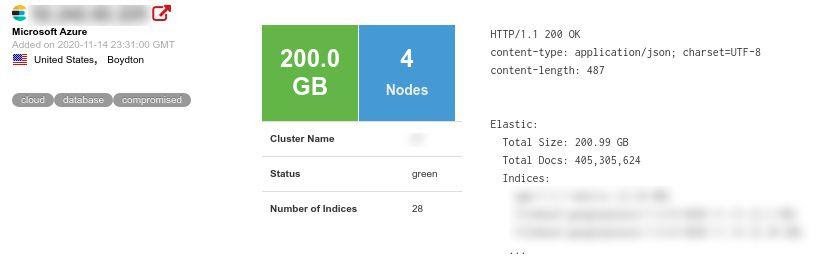
In this instance, the team discovered that Karachi-based company Bykea had exposed all its production server information and allowed access to over 200GB of data containing more than 400 million records showing people’s full names, locations, and other personal information that could potentially be harnessed by hackers to cause financial and reputational damage.
The Elastic instance was left publicly exposed without password protection or encryption, which meant anyone in possession of the server’s IP-address could access the database and potentially remove data from it.
It appeared that in September 2020, Bykea suffered a separate breach, during which unidentified hackers reportedly deleted the company’s entire customer database. At the time, Bykea said it was unaffected by the intrusion because it kept regular backups.
In response, Bykea’s CEO Muneeb Maayr described the cyberattack as “nothing out of the ordinary” given that Bykea is a mobility-based tech firm. It remains unclear whether this latest breach is related to the hack in September.
Who is Bykea?
Founded in 2016 by Pakistani entrepreneur Muneeb Maayr, Bykea is a transportation, logistics and cash on delivery payments company, headquartered in Karachi, Pakistan. The company was one of the first to introduce the novel concept of “motorbike taxis”, used as a means of transport and delivery. Currently, the company offers its range of taxi services in Karachi, Rawalpindi and Lahore.
Bykea also operates as a vehicle-for-hire and parcel delivery company and maintains a software app offering users access to all its services via Google Play and App Store.
The company is an on-demand logistics provider that has embraced mobile demand and ubiquitous internet connectivity to fuel its rapid growth in recent years. The company raised almost US$6 million from private investors in 2019 and followed up by raising a further US$11 million this year. In total, Bykea has raked in US$22 million in private equity from notable investment groups such as Prosus Ventures, Middle East Venture Partners (MEVP) and Sarmayacar since 2016.
What was leaked?
The exposed server contained API logs for both the company’s web and mobile sites and all production server information. The 200GB database containing 400 million records was located on a production server that stores regularly updated data including internal logs including user details.
More specifically, the server contained personally identifiable information (PII) for both customers and contracted employees – their drivers, called “partners” by Bykea.
Bykea customer’s PII:
- Full names
- Phone numbers
- Email addresses
Bykea partners’ (drivers’) PII:
- Full names
- Phone numbers
- Address
- CNIC (Computerised National Identity Card)
- Driver license numbers, issuing city and expiry dates
- Body temperature
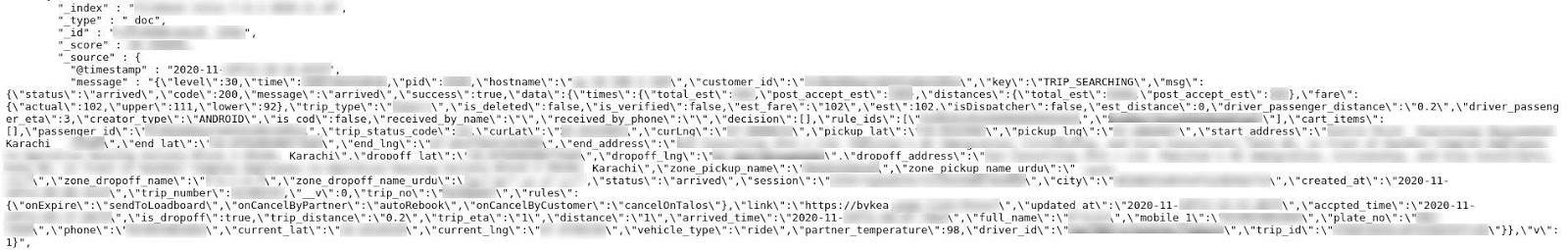
Other information was also left unsecured, such as:
- Internal API logs
- Collection and delivery location information
- User token ID with cookie details and session logs
- Specific GPS coordinates
- Vehicle information including model and number plate
- Driver license expiry information
- Miscellaneous user device information
- Encrypted IMEI numbers
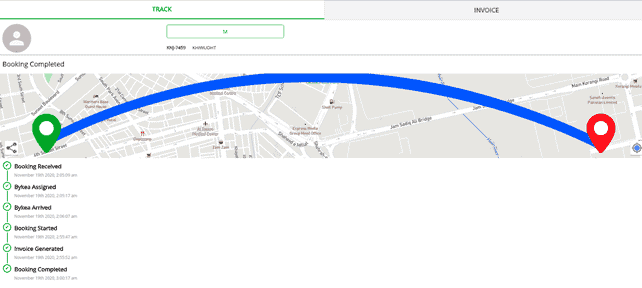
The team discovered Bykea’s server contained customer invoices showing full trip information including where customers were picked and dropped off, driver arrival times, trip distances, fare details and more.
The team also found Bykea’s internal employee login and unencrypted password information on the unsecured server.
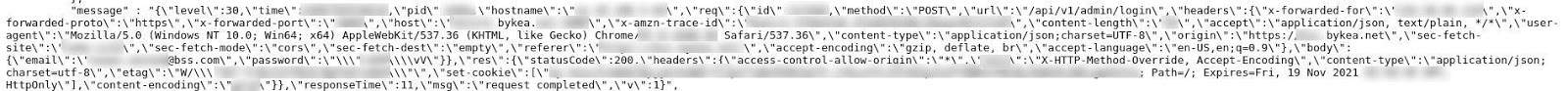
Bykea also had existing commercial relationships with other Pakistani companies including K-Electric, EasyPaisa and JazzCash allowing customers to pay their electricity bills, get cash and send money with the assistance of a Bykea driver and its app. This data was also stored on Bykea’s database and exposed in the leak.

| Number of records leaked: | 400+ million |
| Number of affected users: | Unknown |
| Size of data breach: | 200+ gigabytes |
| Server location: | Boydton, United States |
| Company location: | Karachi, Pakistan |
The security team discovered Bykea’s vulnerability on 14 November 2020. Upon contacting the company on 24 November, Bykea responded immediately by securing its database within 24 hours.
Data breach impact
From the large number of discovered records and the type of information made available, several negative outcomes could occur including identity theft, fraud, and phishing scams.
Full names, residential address details, ID documents like CNIC, online login information and location data could potentially be exploited by nefarious users to target unsuspecting people that registered with the company. Car registration and vehicle data could potentially be used to conduct insurance fraud and other heinous crimes involving stolen identities.
Also, user email addresses could be targeted by hackers who typically use deceptive methods such as infusing leaked customer data into email communications to trigger clickthroughs to malicious websites and installing malicious software.
Moreover, website backend data could be harnessed to exploit Bykea’s internal IT infrastructure including its app and website to generate ransomware attacks or simply to cripple its servers. Back-end technical logs expose not only personal information but also, data that can be weaponised to obtain full control of the server.
Preventing Data Exposure
How can you prevent your personal information from being exposed in a data leak and ensure that you are not a victim of attacks – cyber or real-world – if it is leaked?
- Be cautious of what information you give out and to whom
- Check that the website you are on is secure (look for https and/or a closed lock)
- Only give out what you feel confident cannot be used against you (avoid government ID numbers, personal preferences that may cause you trouble if made public, etc.)
- Create secure passwords by combining letters, numbers, and symbols
- Do not click links in emails unless you are sure that the sender is legitimately who they represent themselves to be
- Double-check any social media accounts (even ones you no longer use) to ensure that the privacy of your posts and personal details are visible only to people you trust
- Avoid using credit card information and typing out passwords over unsecured Wi-Fi networks
- Find out more about what constitutes cybercrime, the best tips to prevent phishing attacks, and how to avoid ransomware
SafetyDetectives.com is the world’s largest antivirus review website. The Safety Detective research lab is a pro bono service that aims to help the online community defend itself against cyber threats while educating organizations on how to protect their users’ data. The overarching purpose of our web mapping project is to help make the internet a safer place for all users.
Bykea’s official statement:
Safety Detectives is a team of online security experts and as ethical hackers reported a vulnerability on one of Bykea’s backup logging nodes in November 2020. The company had attracted interest after a public hacking incident on Aug 31st when Bykea’s database was deleted and it took 24 hours to recover a downtime. Representatives from Bykea were in touch with Safety Detectives who then helped the security team at Bykea solve the vulnerability. Unlike what bloggers in the aftermath of the article on Safety Detectives’ site inferred, this was a vulnerability identification, not a breach of stolen data for criminal purposes. The citation of 400 million files mostly comprises millions of GPS pinpoints that Bykea solicits in tracking over a two week period in 2020 and drivers can rest assured that national ID data is encrypted now on Bykea. Bykea has been on a hiring spree since the middle of 2020, bolstering the engineering team as well as specifically adding dedicated security resources to recognize the importance of this function.
“Information security is a crucial function and protecting consumer information is a key activity in building trust for rapidly growing digital companies like Bykea” said Muneeb Maayr who went on to say: “Security researchers and teams like Safety Detectives play a crucial role in creating awareness and helping companies all around the world identify and plug their weaknesses, a contribution Bykea explicitly welcomes.
Bykea had engaged a multitude of security companies including SecurityWall that ran pen tests on Bykea’s infrastructure and a vulnerability disclosure program with HackerOne. The company is exploring ways to build ongoing collaborations with ethical hackers to advance their mutual interests of building a secure digital economy protecting personal information while empowering consumers with new services and digitally-enabled value propositions. More details on Bykea’s vulnerability disclosure and bug bounty program can be found here: bykea.com/security

Written by Jim Wilson, Security Researcher in the Safety Detective Research Team
Related article: User details of Indonesia’s largest e-commerce platform, Tokopedia, leaked

Be the first to comment